
In the digital age, where healthcare practices increasingly rely on electronic systems to store patient data, manage appointments, and even conduct telehealth sessions, the importance of a comprehensive risk assessment cannot be overstated. As someone with three decades of experience in healthcare IT, I've seen the landscape evolve, and with it, the sophistication of cyber threats. A risk assessment is not just a regulatory checkbox but a fundamental practice that could save your healthcare practice from catastrophic data breaches and financial losses.
Understanding Risk Assessment
A risk assessment is a systematic process of identifying, analyzing, and evaluating the risks associated with the information technology and data handling practices of an organization. In the context of healthcare, it specifically addresses the vulnerabilities that could lead to unauthorized access, use, disclosure, disruption, modification, or destruction of patient health information.
The Importance of Risk Assessment
Why is risk assessment indispensable? Firstly, it's a compliance requirement under the Health Insurance Portability and Accountability Act (HIPAA) Security Rule. Beyond compliance, however, the real value lies in its ability to uncover vulnerabilities in your systems and processes, helping you to mitigate risks before they can be exploited by cybercriminals. In essence, it's about protecting your patients' sensitive information, preserving their trust, and safeguarding the reputation and financial viability of your practice.
Steps to Conducting a Risk Assessment
- Identify the Scope of the Assessment:
- Determine which systems, data, and processes will be evaluated. This includes all electronic devices, software, and data storage solutions used in your practice.
- Gather Information:
- Collect all relevant information about the IT infrastructure, including network diagrams, data flow charts, and an inventory of all hardware and software.
- Identify Potential Threats and Vulnerabilities:
- List all possible threats (e.g., malware, hacking, insider threats) and vulnerabilities (e.g., outdated software, weak passwords) that could impact the confidentiality, integrity, and availability of ePHI.
- Assess Current Security Measures:
- Review existing security measures to determine their effectiveness in protecting against identified risks. This includes physical security, cybersecurity policies, employee training programs, and more.
- Determine the Likelihood and Impact of Risks:
- Evaluate how likely it is for each identified risk to occur and what the potential impact would be on your practice.
- Prioritize Risks and Develop an Action Plan:
- Based on the likelihood and impact, prioritize the risks and develop a comprehensive action plan to mitigate them. This plan should include specific security measures, responsible parties, and timelines.
- Implement the Action Plan:
- Take concrete steps to address each risk, whether through technological solutions, policy changes, or staff training.
- Document Everything:
- Keep detailed records of the risk assessment process, findings, and remediation actions. This documentation is essential for compliance and for future assessments.
- Review and Update Regularly:
- Cyber threats are constantly evolving, so it's important to review and update your risk assessment and action plan regularly.
Let's visualize some of the most common vulnerabilities in healthcare IT systems through an infographic. This graphic will highlight areas such as:
- Outdated Software: Often lacking critical security patches, making them easy targets for attackers.
- Weak Password Policies: Simple or reused passwords can be easily cracked, giving hackers easy access.
- Inadequate Employee Training: Untrained staff may fall victim to phishing scams or inadvertently disclose sensitive information.
- Lack of Data Encryption: Unencrypted data is susceptible to interception during transmission or theft.
- Insufficient Network Security: Without proper safeguards, networks can be breached, exposing all connected systems and data.
Number of Common IT Security vulnerabilities and exposure (CVEs) worldwide from 2009 to 2024 YTD
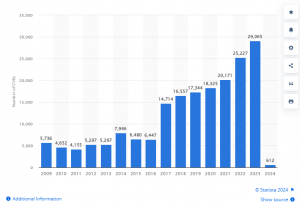
source: https://www.statista.com/statistics/500755/worldwide-common-vulnerabilities-and-exposures/
By understanding these vulnerabilities and conducting a thorough risk assessment, healthcare practices can significantly enhance their cybersecurity posture. It's about being proactive rather than reactive, ensuring that your practice is not just compliant, but truly secure. As we continue to navigate the complexities of healthcare IT, let's prioritize the safety and security of the sensitive information entrusted to us by our patients.


