Scorpion IT Support
Technology Business Review: Annual IT & Security Report Card
This page explains the standards used in your annual Technology Business Review (TBR). The TBR provides a report‑card style assessment of your IT infrastructure and cybersecurity posture—focused on practical controls that support stability, security, and business continuity.
Executive Summary
The Annual IT & Security Report Card is designed to keep the report clean and easy to read. Each area below links to details so business owners and managers can understand what is included, why it matters, and how it is evaluated.
- Clear grading: Strong / Acceptable / Needs Attention
- Industry alignment: Built on recognized guidance such as the NIST Cybersecurity Framework
- Layered approach: Multiple safeguards working together (no single tool is expected to stop everything)
NIST Standards We Reference
Our layered cybersecurity standards and the annual report card structure are informed by widely recognized guidance, including the NIST Cybersecurity Framework and its supporting materials. These resources help organizations identify risk, apply consistent protections, detect suspicious activity, respond effectively, and recover reliably.
Primary references
Report Card Areas
Each area below is part of the Annual IT & Security Report Card. Use these links for full details while keeping the one‑page report clean. (Tip: You can link directly to each section from your PDF report card using these anchors.)
1) Compliance & Policy Enforcement
Policies are the foundation of a secure environment. This area covers practical standards for acceptable use, access rules, device requirements, and enforcement—ensuring everyone follows consistent expectations that support security and day‑to‑day operations.
What we evaluate
- Acceptable use & access standards
- Administrative privilege controls
- Device baseline requirements
- Consistency across users and systems
Why it matters
- Reduces avoidable risk and confusion
- Supports compliance and cyber insurance expectations
- Improves operational consistency
2) Backup & Disaster Recovery
Backups are your safety net. This area evaluates whether critical business data and cloud systems are backed up properly, protected from tampering, and can be restored within a reasonable timeframe.
What we evaluate
- Backup scope (servers, cloud, endpoints where applicable)
- Retention & versioning
- Recovery readiness and testing
- Ransomware-resistant backup practices
Why it matters
- Fast recovery from outages and cyber incidents
- Reduces downtime and financial loss
- Protects against accidental deletion
3) Monitoring & Incident Response (24×7 SOC)
Prevention is important, but detection and response is what keeps small issues from becoming major incidents. This area reviews alerting coverage, monitoring visibility, response readiness, and clear escalation paths.
What we evaluate
- 24×7 monitoring coverage and alert routing
- Log visibility (identity, endpoints, email where available)
- Incident response process and documentation
- Escalation timelines and communication
Why it matters
- Faster containment of threats
- Reduces business impact
- Improves decision-making during incidents
4) Network Security
The network is still a critical control layer. This area focuses on keeping the “blast radius” small by enforcing proper firewall policies, secure remote access, and network segmentation (where appropriate).
What we evaluate
- Firewall configuration and rule hygiene
- Secure remote access controls
- Network segmentation (VLANs) & guest Wi‑Fi separation
- DNS filtering and threat blocking (where in scope)
Why it matters
- Limits lateral movement if an account or device is compromised
- Improves stability and performance
- Supports compliance and cyber insurance reviews
5) Email Security & Anti‑Phishing
Email is still the most common entry point for business compromises. This area evaluates protections that reduce phishing, impersonation, malicious links/attachments, and suspicious mailbox behavior.
What we evaluate
- Inbound filtering and threat detection
- Impersonation and spoofing protections
- Link/attachment inspection where supported
- Mailbox monitoring and alerting (when available)
Why it matters
- Reduces click‑risk and credential theft
- Prevents invoice fraud and business email compromise
- Improves trust and communication integrity
6) Endpoint Protection (AV & EDR)
Endpoint security has evolved beyond basic antivirus. This area evaluates layered endpoint controls, including behavior-based detection (EDR), device encryption readiness, and standards that reduce attack surface.
What we evaluate
- Endpoint protection coverage and policy enforcement
- Behavior-based detection and isolation capability
- Disk encryption readiness and standards
- Patch posture and baseline configuration (where in scope)
Why it matters
- Stops malware and reduces dwell time
- Improves visibility for incident response
- Protects data on lost or stolen devices
7) Identity & Access Management
Attackers increasingly target accounts rather than devices. This area reviews password standards, MFA, least privilege, and safeguards designed to reduce modern identity threats—including attempts to abuse or bypass MFA through social engineering and session theft.
What we evaluate
- MFA enforcement and sign‑in controls
- Least privilege and admin access restrictions
- Suspicious sign‑in monitoring and alerts
- Conditional access patterns (where supported)
Why it matters
- Reduces account takeovers and “quiet” compromises
- Improves auditability and accountability
- Supports secure remote work
8) User Awareness & Training
Security improves when users understand what “good” looks like. This area evaluates the cadence and quality of awareness training, phishing readiness, and reinforcement of policies.
What we evaluate
- Training cadence and participation
- Phishing awareness and reporting habits
- Policy reinforcement and reminders
- High‑risk workflow guidance (payments, vendor changes, etc.)
Why it matters
- Reduces phishing success rates
- Builds a consistent security culture
- Supports compliance expectations
9) Hardware Infrastructure
Reliable hardware is the foundation for uptime, performance, and secure configurations. This area reviews lifecycle, supportability, and whether devices meet baseline requirements for modern security (such as encryption support).
What we evaluate
- Hardware lifecycle and replacement planning
- Warranty/support status for critical systems
- Performance readiness (SSD, RAM, firmware support)
- Security readiness (TPM, encryption support where applicable)
Why it matters
- Reduces downtime and recurring issues
- Improves patching and security compatibility
- Stabilizes day‑to‑day business operations
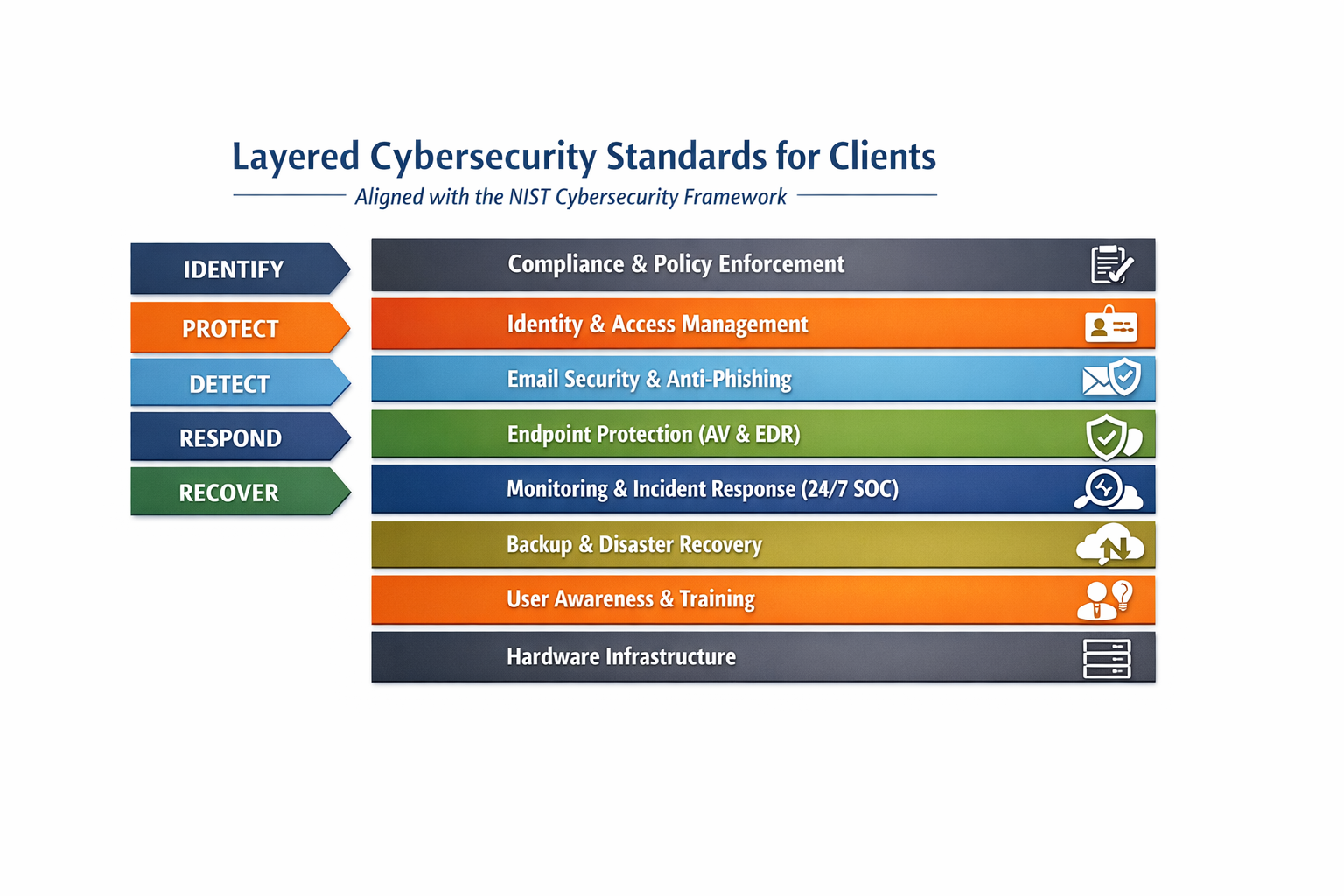
Layered Cybersecurity Standards Graph
This diagram supports the report card by showing how each layer works together. If one layer is bypassed, another layer is designed to detect, contain, or help the business recover.
Questions or want to review your scorecard?
If you’d like us to walk through your annual Technology Business Review, we’re happy to schedule an in person meeting and clarify any recommendations.Pl


